Pull requests testing
In Buddy, you can test and deploy pull requests using pipelines. Every time a pull request is created and/or a push is made to the corresponding branch, Buddy will automatically run the defined pipeline and send its execution status to GitHub.
Forks and branches
You can create pull requests within the same repository or a forked repository. If you run all pull requests within one repository and you don't work on a fork model, then it's enough to create a pipeline with * wildcard to test your pull requests. The pipeline will be run after every push to any branch in your repository. Thanks to that, each commit will be tested straight away and when you open a pull request, it will be marked with a status depending on the tests' result.
For security reasons, support for pull requests originating from forks is disabled by default.
To enable it:
- Go to Project Settings in the left column.
- Scroll down to the OPTIONS section.
- Select the Pull requests support option to activate the feature:
Image loading...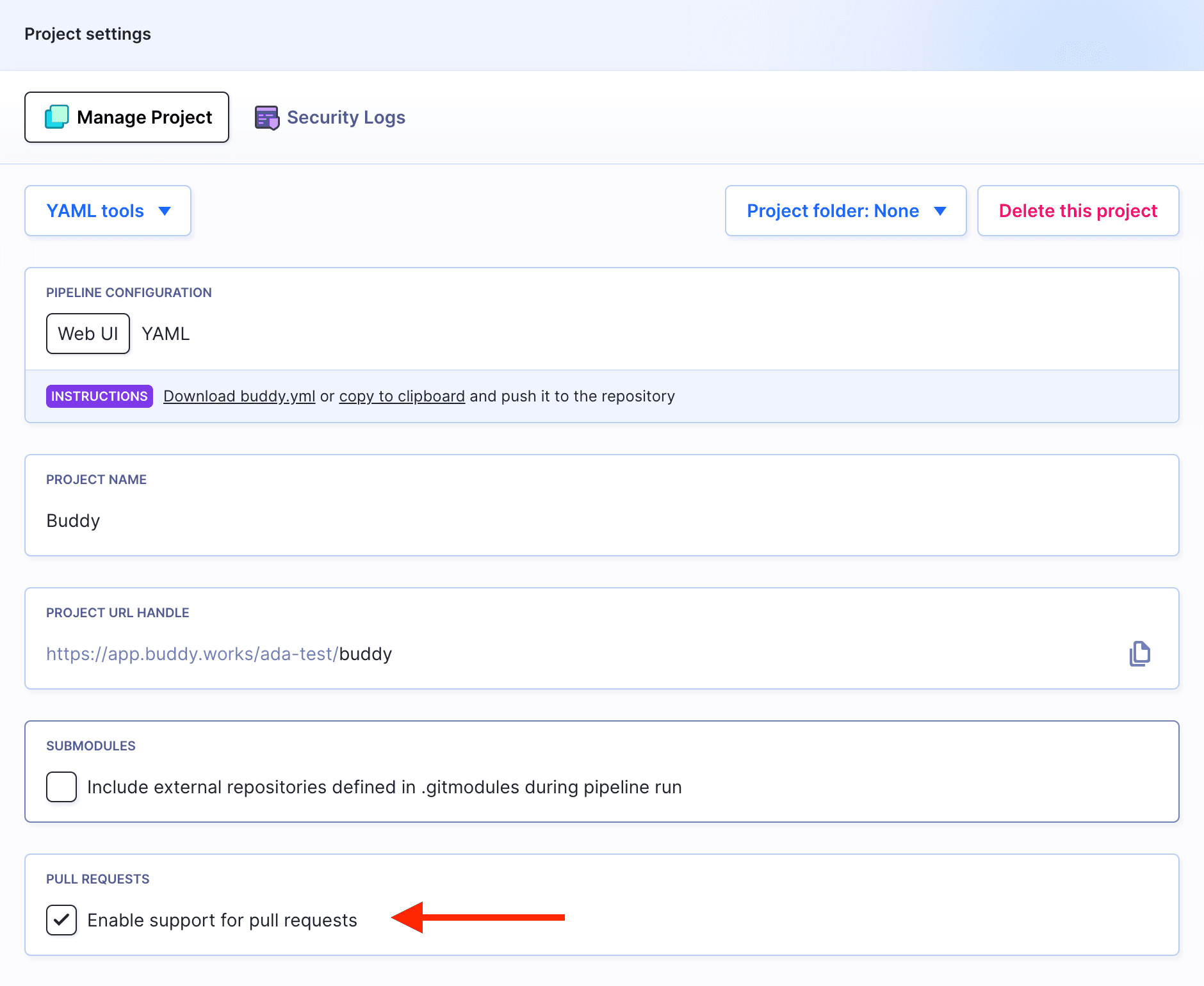
Once you turn this option on, you'll be able to select Add all pull requests as the ref when specifying the Git event:
Image loading...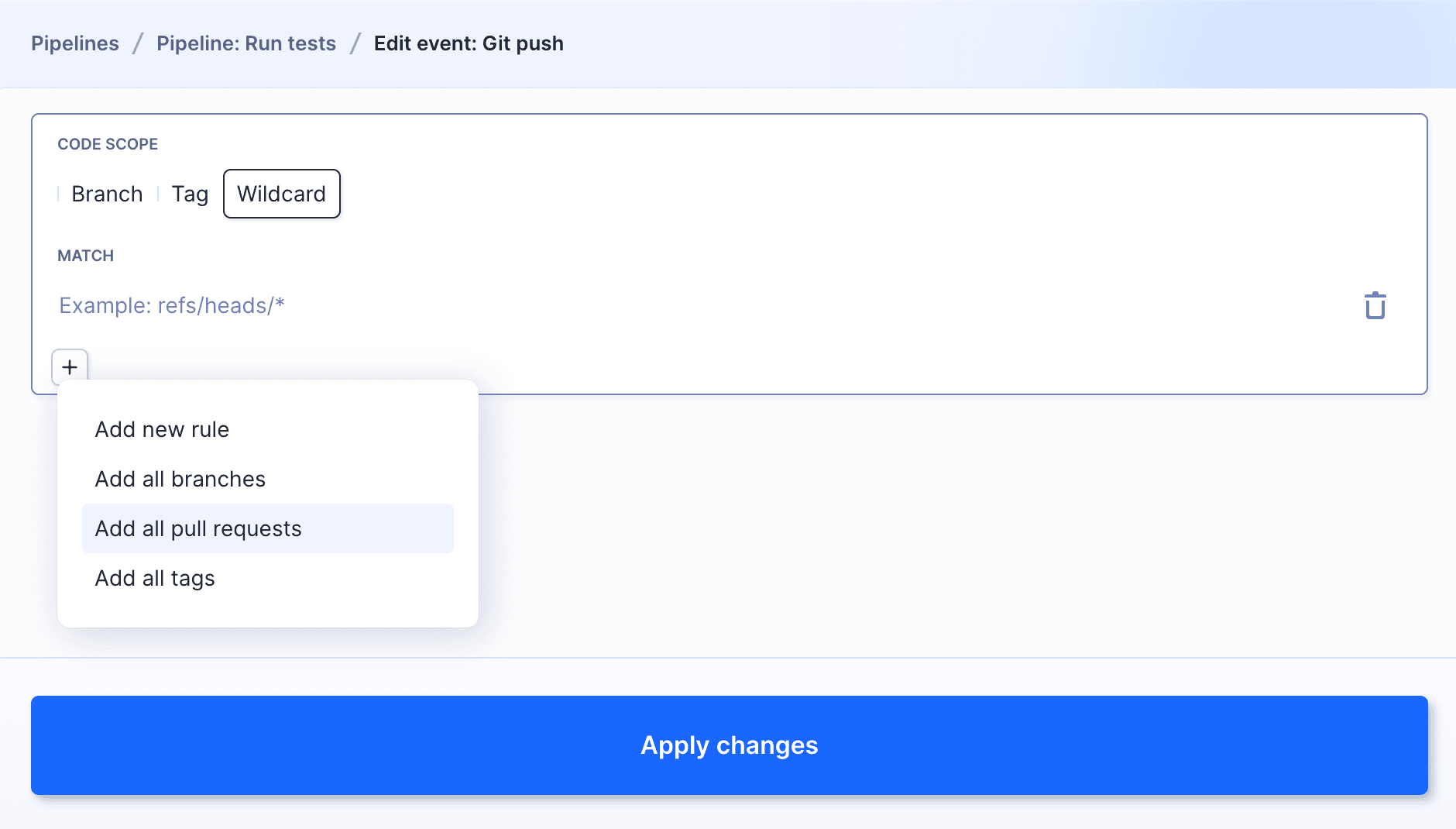
refs/pull/* wildcard instead of a single * with the Add all pull requests option. Using the * wildcard causes the pipeline to run twice for all PRs that from within the same repository. The pipeline will run triggered by the commit pushed to the branch and then because a new commit is detected in the PR even though this is a single event.
Pipeline actions
With PRs enabled, you can now add a testing action to the pipeline:
Image loading...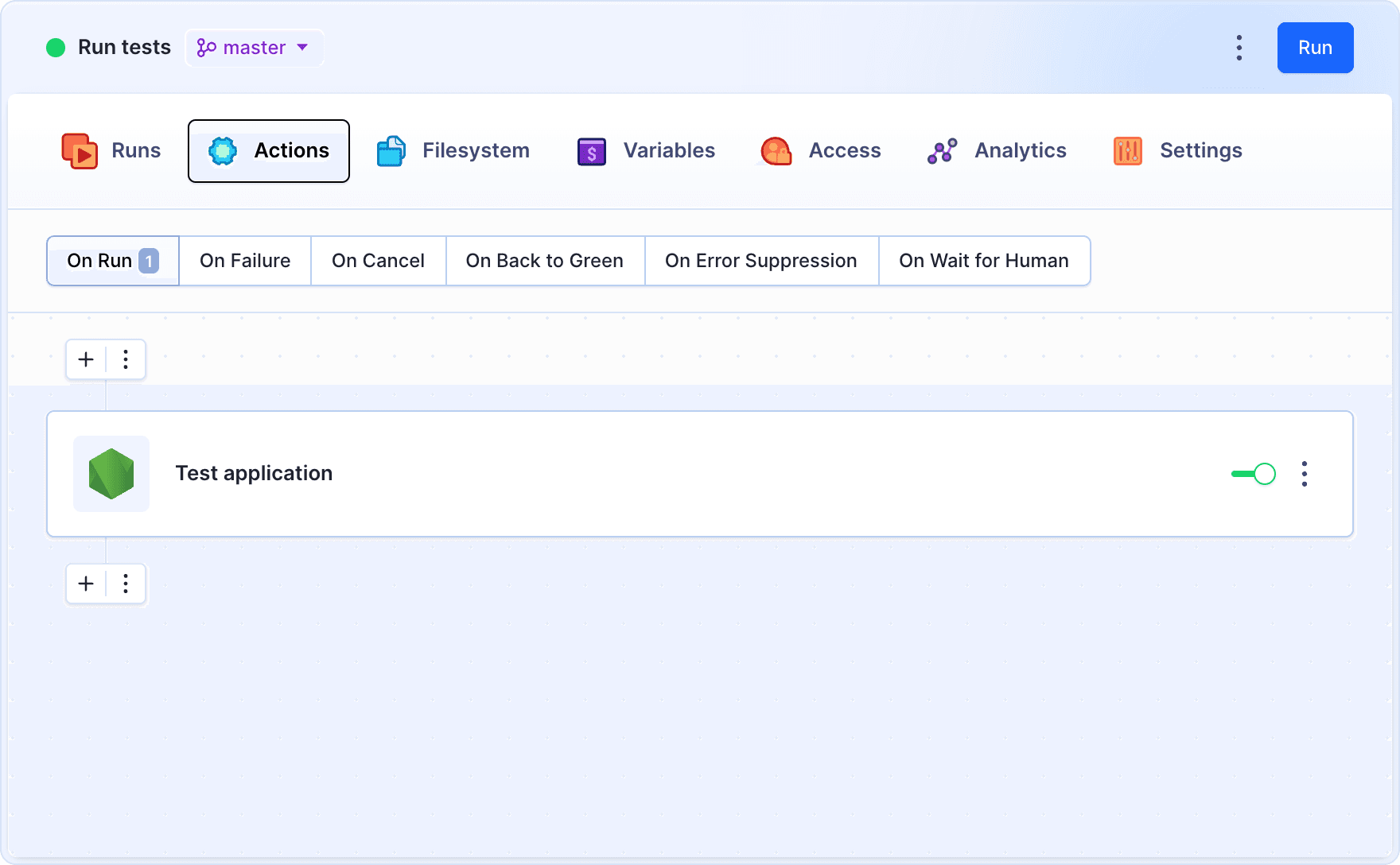
Finally, let's add a notification action in the On Failure section that will notify us in case something goes wrong:
Image loading...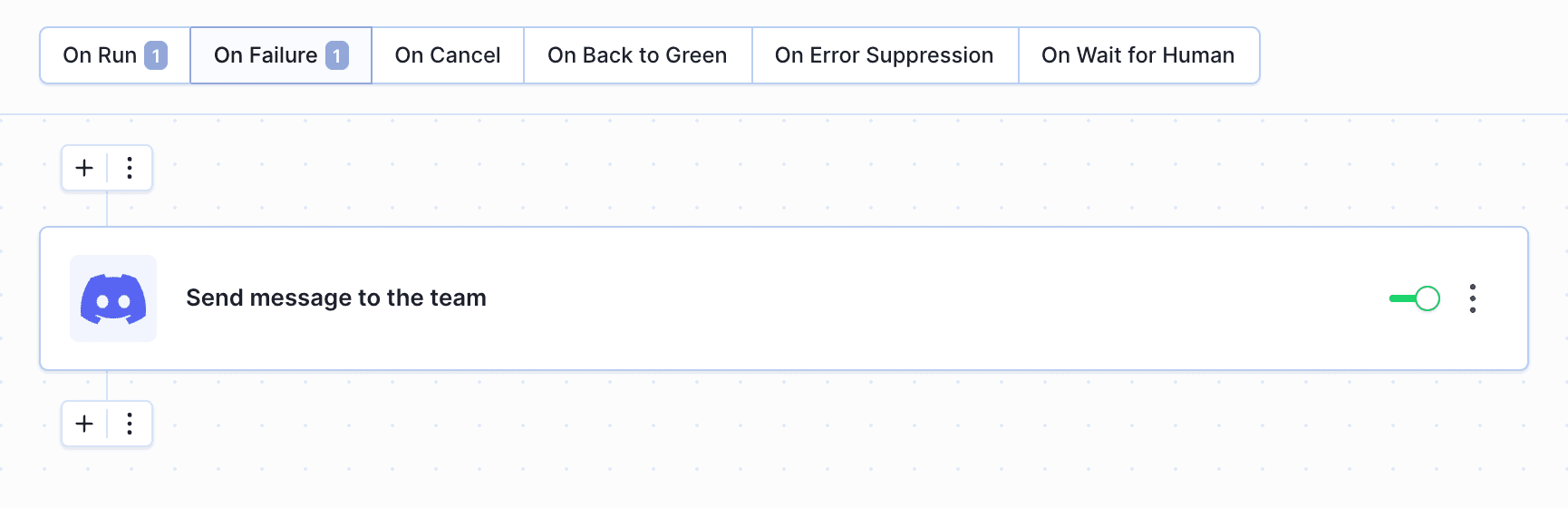
Automatic merge
Once you ensure that everything’s fine, switch to GitHub and configure the branch protecting rule for Buddy. Enable auto-merge, and you receive a fully-working Continuous Deployment pipeline:
Image loading...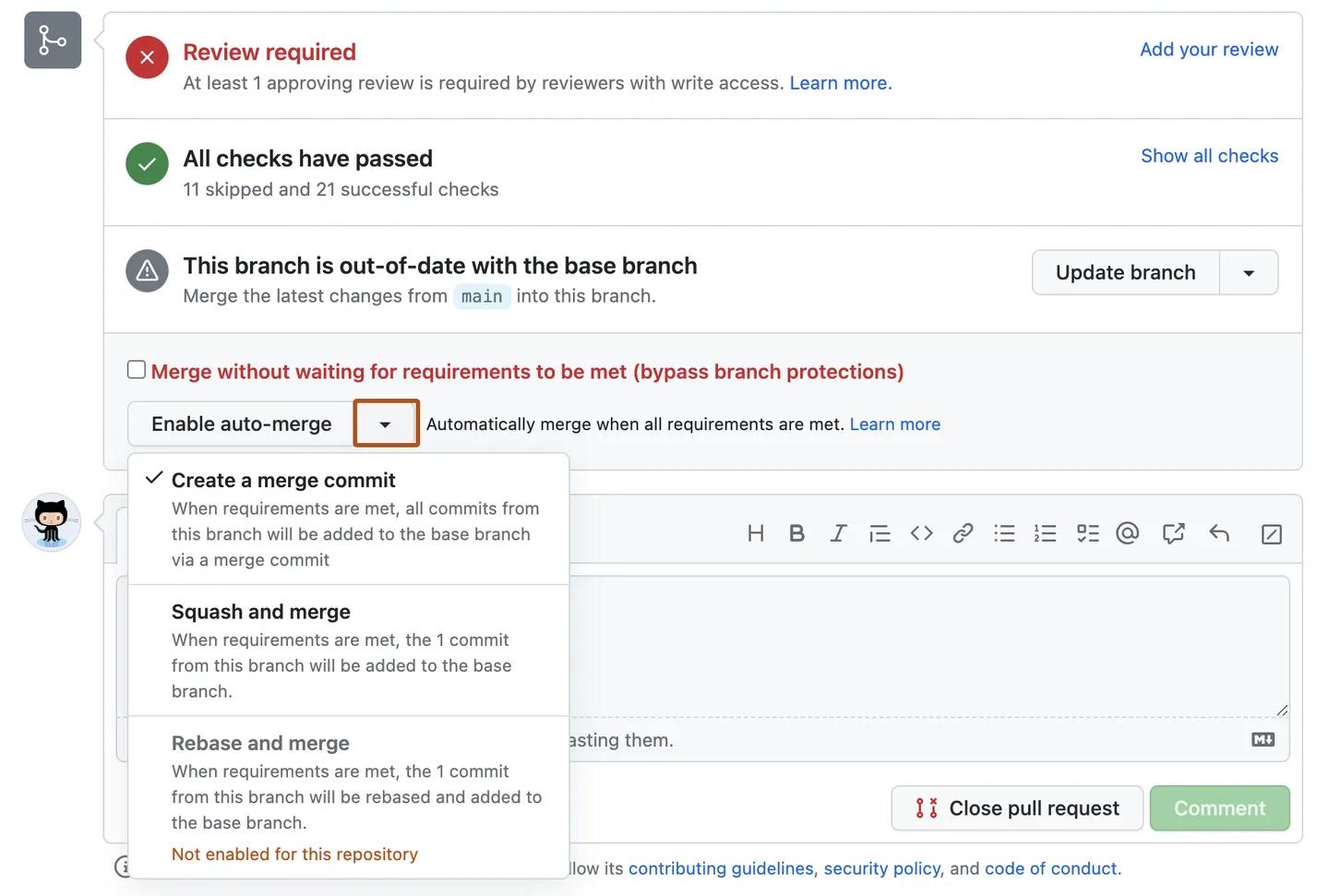
Security
Last modified on Jan 30, 2026