Trust Conditions for OIDC Identity Provider
Trust conditions control which external service tokens are accepted by Buddy. Conditions are combined using if and and operators.
Trust Conditions for GitHub Actions
For GitHub Actions, you can use the following claims in trust conditions:
Warning
For GitHub Actions, the
repository_owner trust condition is the minimum requirement for proper configuration.
Image loading...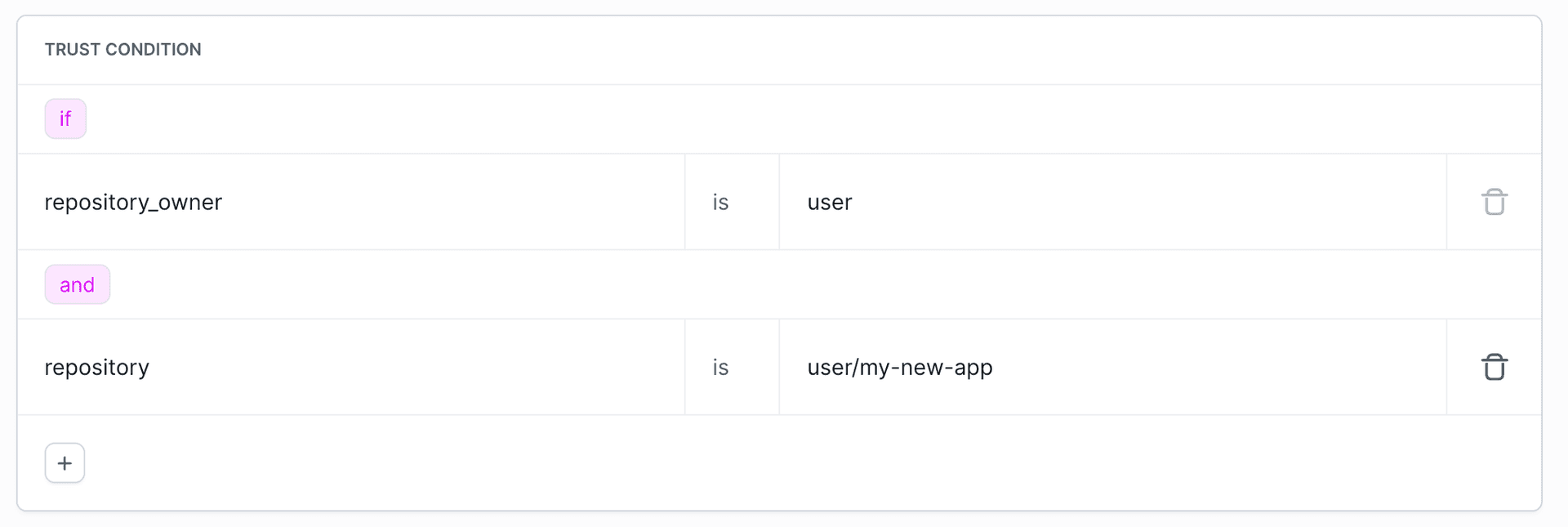
| Condition | Description | Example |
|---|---|---|
| repository_owner | GitHub organization or user | octo-org |
| sub | Subject identifier | repo:octo-org/octo-repo:environment:prod |
| repository | Full repository name | octo-org/octo-repo |
| ref | Git reference (branch or tag) | refs/heads/main |
| ref_type | Reference type | branch |
| actor | GitHub user who triggered the workflow | octocat |
| workflow | Workflow name | example-workflow |
| job_workflow_ref | Job workflow reference | octo-org/octo-automation/.github/workflows/oidc.yml@refs/heads/main |
| aud | Audience | https://github.com/octo-org |
| environment | Deployment environment | prod |
| repository_visibility | Repository visibility | private |
| run_id | Workflow run ID | example-run-id |
| run_number | Workflow run number | 10 |
| event_name | Event that triggered the workflow | workflow_dispatch |
| sha | Commit SHA | example-sha |
| actor_id | GitHub user ID | 12 |
Trust Conditions for CircleCI
For CircleCI, you can use the following claims in trust conditions:
Image loading...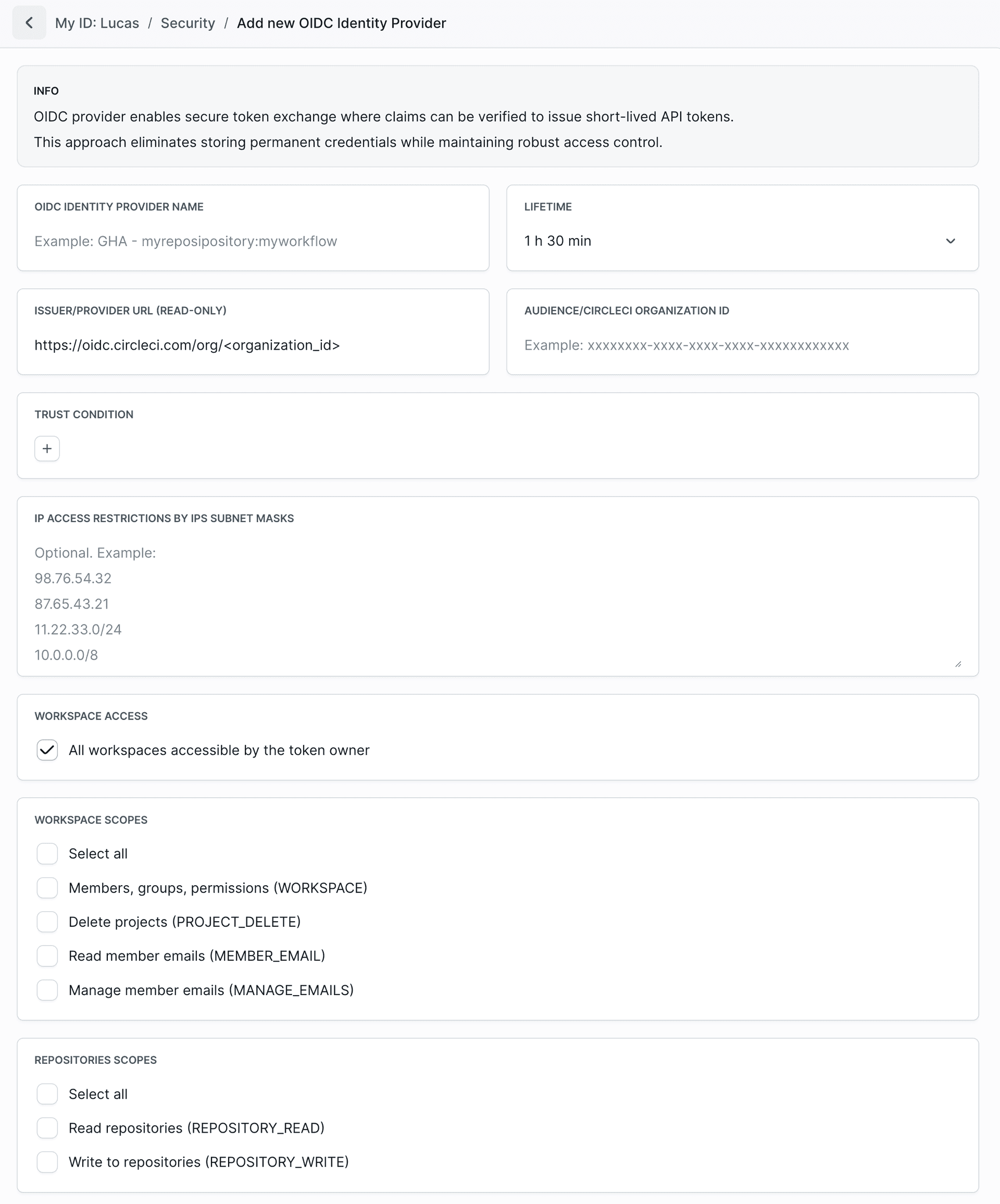
| Condition | Description | Example |
|---|---|---|
| oidc.circleci.com/project-id | Project UUID where the job is running | 23e4567-e89b-12d3-a456-426614174000 |
| oidc.circleci.com/vcs-origin | Repository URL that triggered pipeline | github.com/organization-123/repo-1 |
| oidc.circleci.com/vcs-ref | Reference to change that triggered the pipeline | refs/heads/main |
| oidc.circleci.com/context-ids | Context UUIDs used in the job | ["a1b2c3d4-e5f6-7890-abcd-ef1234567890"] |
| oidc.circleci.com/ssh-rerun | Whether job uses SSH rerun feature | true, false |
| sub | Subject identifier (org/project/user) | org/<org_id>/project/<project_id>/user/<user_id> |
Trust Conditions for Other Provider
For Other Provider, enter custom key/value based on your OIDC token claims. Check your provider's documentation for available claims.
Trust Conditions Examples
Examples for GitHub Actions
Basic example - Repository Owner (minimum):
if repository_owner is "octo-org"
Advanced example - Repository and Branch:
if repository_owner is "octo-org"
and repository is "octo-org/octo-repo"
and ref is "refs/heads/dev"
and ref_type is "branch"
Image loading...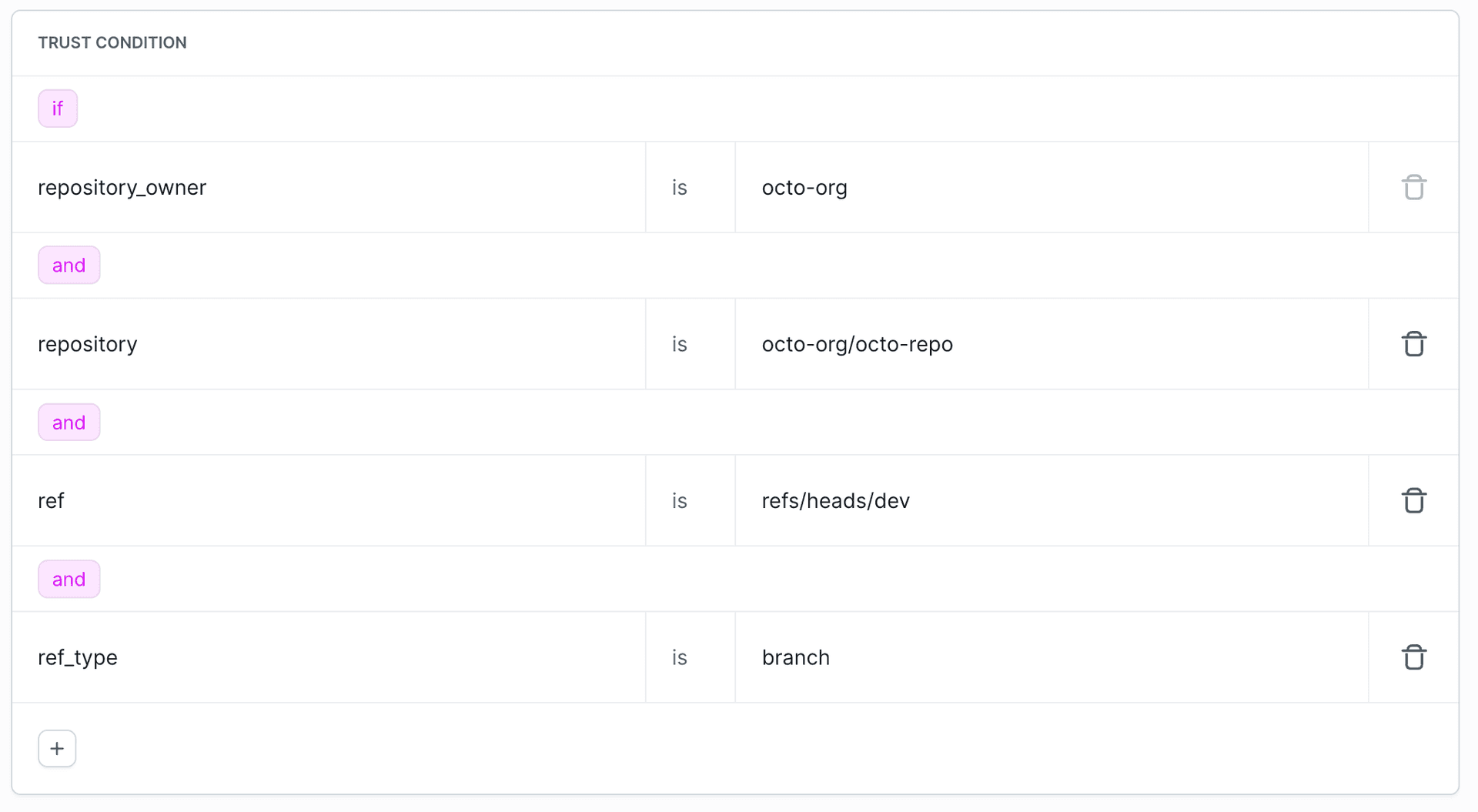
Examples for CircleCI
Basic example - Project ID:
if oidc.circleci.com/project-id is "23e4567-e89b-12d3-a456-426614174000"
Advanced example - Project ID, VCS Origin, and VCS Ref:
if oidc.circleci.com/project-id is "23e4567-e89b-12d3-a456-426614174000"
and oidc.circleci.com/vcs-origin is "github.com"
and oidc.circleci.com/vcs-ref is "refs/heads/main"
Related documentation
- GitHub Actions - GitHub Actions configuration
- CircleCI - CircleCI configuration
- Other Provider - Other provider configuration
Last modified on Feb 19, 2026